Rene Lansink, Sales Acceleration Director EMEA - With more than 20 years in the industry, I’ve seen how challenges – and opportunities – around identity have evolved, especially within financial services. In the early days, identity and access management (IAM) was straightforward. It centered around passwords: granting entry to a single, often on-premises system. As networks grew more interconnected, centralized user management became essential. Tools like LDAP and Active Directory environments emerged, primarily to manage internal employees (B2E).
As organizations began relying on multiple systems, user expectations shifted. Single Sign-On (SSO), using standards like SAML and OAuth, streamlined access and enabled secure external collaboration. This marked the beginning of on-prem IAM – not just for internal users, but for B2B scenarios as well.
Then came the cloud – and with it, a shift in how we think about identity. IAM-as-a-service (IDaaS) secured hybrid environments without compromising user experience. Multi-Factor authentication (MFA) became a necessity, while API and SDK-based integrations broadened application connectivity.
What about today’s B2C and B2B use cases?
IAM began with internal users – employees verified through payroll and ID checks. Complexity grew with the rise of contractors, freelancers and temporary workers. The rise of B2C apps shifted priorities to scale and convenience. Social logins and passwordless authentication quickly took hold (trends accelerated by COVID). At Auth0, I saw the demand surge, driving a wave of innovation across the B2C space.
Meanwhile, regulatory pressures intensified. Frameworks like GDPR, DORA, NIS2, and Schrems II/III raised compliance standards, prompting companies to rethink how they manage customer identity. Technologies like digital sovereignty, biometrics, NFC, and risk-based authentication are no longer optional – they're foundational.
The rise of complex B2B identities, and why national banks should take notice

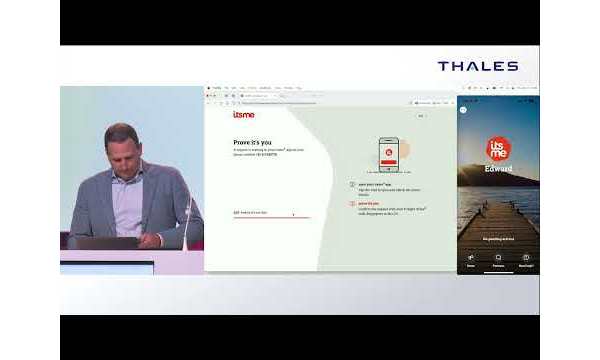
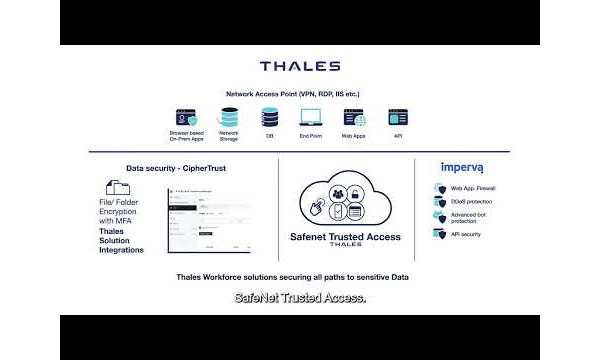
As B2E and B2C identity matured, B2B use cases began to grow more complex – especially across financial ecosystems. National banks and insurers now need to securely connect with partners, subsidiaries, service providers, intermediaries, and even other banks. This requires precise identity management – not just of organizations, but of individual roles within them. Tools like MFA, OTP, biometric passkeys, and QR codes help enable secure, seamless access. EU-wide identity wallets are also on the horizon (more on that in another article).
Some have tried to combine B2C and B2B IAM into one system, but the differences in user experience, security and control are too great. B2B demands more granular access – think of an Active Directory, but designed for external users and complex application permissions.
To manage this complexity, capabilities like federation and delegated user management are becoming increasingly important. These approaches help answer the critical question: Who should have access? And who within each partner organization is responsible for managing that access? Identity brokering with providers such as DigiD or Microsoft Entra ID is gaining traction, too.
But identity in B2B isn’t just limited to people anymore. APIs, containers, IoT devices, and software agents – even scripts – now require secure identities and access controls. As machine-to-machine (M2M) authentication becomes a core part of a modern identity strategy, it brings new layers of complexity and opportunity – while I’ll explore further in a later article.